The Data Center as the New Vault: Infrastructure Considerations for Modern Trust Administration
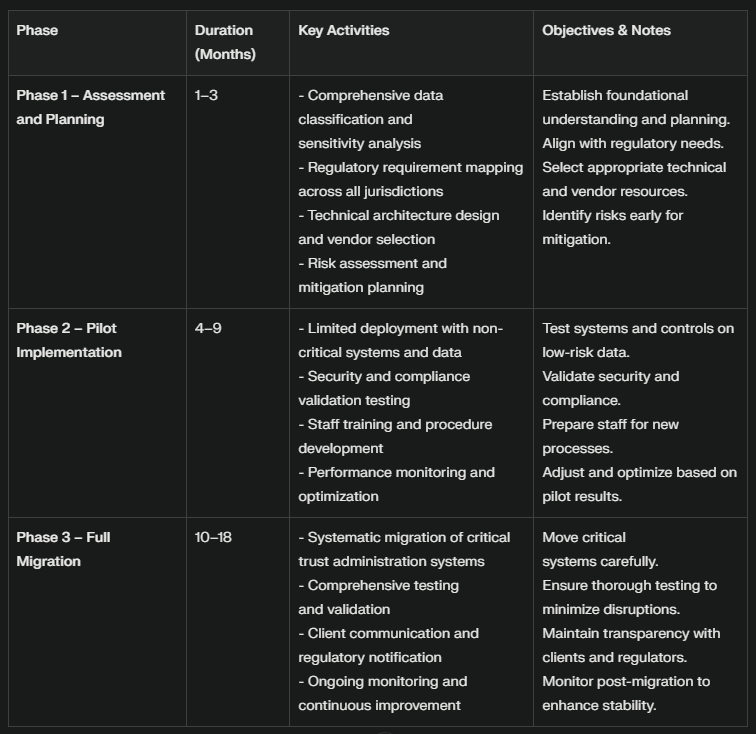
Phased Implementation Strategy:
Phase 1 - Assessment and Planning (Months 1-3):
Comprehensive data classification and sensitivity analysis
Regulatory requirement mapping across all operational jurisdictions
Technical architecture design and vendor selection
Risk assessment and mitigation planning
Phase 2 - Pilot Implementation (Months 4-9):
Limited deployment with non-critical systems and data
Security and compliance validation testing
Staff training and procedure development
Performance monitoring and optimization
Phase 3 - Full Migration (Months 10-18):
Systematic migration of critical trust administration systems
Comprehensive testing and validation procedures
Client communication and regulatory notification
Ongoing monitoring and continuous improvement
Change Management:
Comprehensive staff training programs addressing new procedures and capabilities
Client communication strategies explaining infrastructure improvements and benefits
Regulatory engagement ensuring compliance throughout transition process
Continuous monitoring and feedback collection for ongoing optimization
Regulatory Engagement Strategy
Proactive Regulatory Communication
Preparation for Regulatory Discussions:
Infrastructure Documentation: Comprehensive documentation of data flows, security controls, and access procedures
Compliance Mapping: Clear demonstration of how infrastructure choices support regulatory compliance
Risk Assessment: Detailed analysis of infrastructure-related risks and mitigation strategies
Incident Response Planning: Clear procedures for addressing infrastructure-related incidents and regulatory notification
Ongoing Regulatory Relationship Management:
Regular briefings on infrastructure changes and improvements
Proactive sharing of security incident reports and remediation actions
Participation in regulatory forums discussing infrastructure and technology trends
Collaboration with industry peers on best practice development and regulatory guidance
Final Thoughts
Infrastructure decisions in modern trust administration represent fundamental choices about risk, control, and strategic positioning rather than merely operational considerations. The digitization of fiduciary services demands that trustees approach infrastructure architecture with the same rigor applied to investment policy and regulatory compliance frameworks.
The choice between cloud, sovereign, or hybrid infrastructure models must align with each institution's regulatory environment, risk appetite, operational capabilities, and strategic objectives. There is no universal solution—only architectures that are more or less aligned with specific fiduciary requirements and institutional contexts.
As the World Economic Forum notes, "The age of technological rivalry is here, but whether data centres become targets of conflict or backbones of a connected global economy will depend on choices made now by policy-makers and industry leaders." For trustees, these choices extend beyond technology to encompass fundamental questions of fiduciary stewardship in an increasingly complex global environment.
Successful trustees will be those who recognize infrastructure not merely as operational support, but as fiduciary infrastructure—a critical component of their ability to fulfill duties of care, loyalty, and prudence in an increasingly digital world. The institutions that thoughtfully align their technological architecture with their fiduciary responsibilities will be best positioned to serve clients effectively while maintaining regulatory confidence and competitive advantage.
The path forward requires neither defaulting to convenience nor pursuing control for its own sake, but rather designing infrastructure architectures that serve the deepest principles of fiduciary duty while embracing the operational advantages that modern technology can provide.